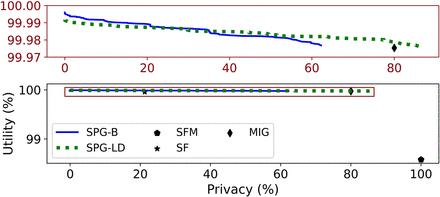
Figure 6.
Adaptive threshold attack model, in which the attacker leverages correlation data, baselines flip SNVs.K = 5, baselines only flip SNVs.
(Downloading may take up to 30 seconds. If the slide opens in your browser, select File -> Save As to save it.)
Click on image to view larger version.

Adaptive threshold attack model, in which the attacker leverages correlation data, baselines flip SNVs.K = 5, baselines only flip SNVs.